6 minutes
Azure Sentinel: SIEM for all?
Every now and again I post something on Twitter that seems to resonate and prompt more of a reaction than I expect… a recent example - and ironically the reason that I decided to bite the bullet with this blog - was the tweet below regarding the (now not so) new release of Azure Sentinel; Microsoft’s answer to SIEM for the modern Enterprise:
Spent some time configuring @Azure #Sentinel today... Previous experience of #SIEM = painful deployment, immediate log fatigue, and questionable "useful" insights. #Sentinel was running in less than an hour and is adding immediate value. What a tool! 😍 @Microsoft #Security
— Kelvin Papp (@kelvinpapp) March 2, 2019
Why does this excite me so much? I’ve spent a good chunk of my career in security-centric roles for one reason or another. The first “proper” IT role I had was with an Aerospace & Defence organisation who (naturally) placed a significant emphasis on security. My progress at that company culminated in a role as a security lead for a major integration project, which in turn played a significant part in allowing me to develop a range of skills that have held me in good stead for the last 10+ years. More recently I held a position as a Security Product Manager for a large MSP, and right now an element of my role involves ensuring we remain technically compliant with our obligations under Cyber Essentials and ISO 27001…
In short, I seem to gravitate towards the murky, yet fascinating world of IT security and announcements like this get me far more excited than perhaps they should do…!
The Problem…
The problem with “IT security”, as I’ve come to learn over the years, is that it’s shrouded in so much complexity and jargon that it’s seen as a burden to most organisations - particularly those that lack the in-house resource to be able to give it the focus it needs. Most understand the concept and need for a firewall, for decent antivirus, perhaps even going as far as adopting MDM / MAM solutions or cloud filtering services, but few proactively monitor or manage the activity in their environment to the extent where they can detect not just clear-cut attacks or violations, but suspicious or preparatory activity by “bad actors”. The calm before the storm!
Doing security “properly” is typically the domain of the enterprise - specialist tool-sets and dedicated, expensive expertise to monitor and decipher all of the underlying (often hidden) “noise” that provides the real view of what’s going on. One of the biggest contributions to this analysis usually comes in the form of SIEM (Security Information and Event Management) software which collates and analyses signals from across the infrastructure and network, providing insights based on predefined or automated logic. The biggest challenge with these tools is that by nature they surface noise. Lots of it.
The Reality…
In spite of best intentions and significant progress in recent years, false-positives are part of the daily life of those that work in SecOps. Minimising these requires customisation and tuning, training systems to understand “normal”, and a constant battle to ensure legitimate concerns aren’t buried. I’ve had the “joy” (yes, that’s serious and sarcastic!) of working with some of the leading tools in this space and not one has “just worked” in the way that many vendors tell you they will. The net result is time and effort - at great cost - for solutions that often end up being a significant drain on IT departments, or worse still, ignored until it’s too late.
This shouldn’t really be a surprise. Security is complex, and as a result is costly. But should it be? Should smaller organisations find themselves exposed to risks that could be avoided because they don’t have deep pockets? Should organisations be forced into hiring security experts at great cost? (sorry, security friends!). Possibly not for much longer.
A Solution?
Enter Azure Sentinel. I saw the announcement on launch day and I have to be honest - I wasn’t overly hopeful. Microsoft have made significant strides into the Security space in the last couple of years, but a proper contender for Enterprise SIEM? I’d heard rumours of a product in the works and expected something that would better accommodate Azure workloads, integrate with Platform Services, and potentially represent a step into the “as a Service” world . I didn’t expect it to be all of those things and then some. I especially didn’t expect it to trigger a change in my thinking towards SIEM through it’s addressing of many of the challenges that I associate with products of old (as above).
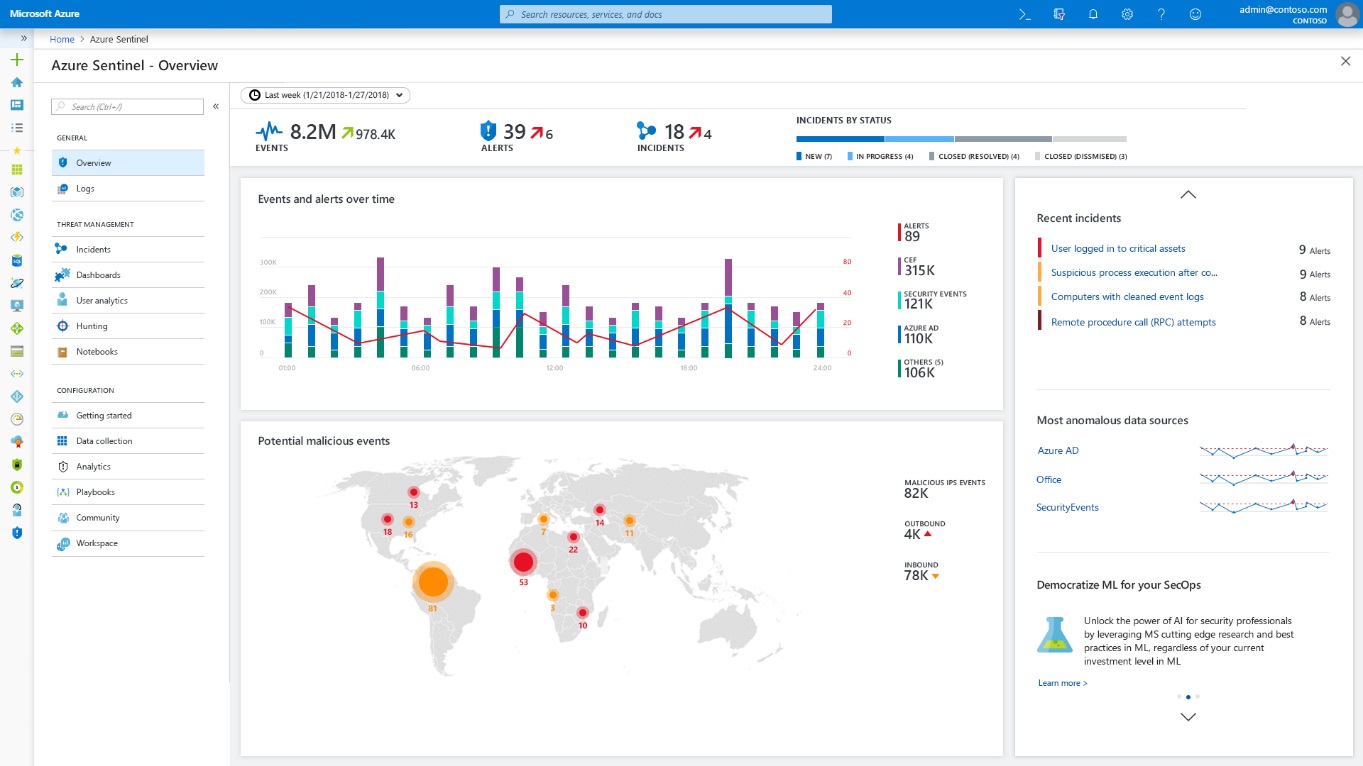
So what’s different? For one, it deploys in minutes (no exaggeration). I was able to stand up an Azure Sentinel instance, integrate it with half a dozen or so (Microsoft) cloud services, and started to see data flowing into my workspace within about 15 minutes. It also takes advantage of the platform it sits on, leveraging the significant scale of Azure to assist with event correlation, and Machine Learning to identify suspicious patterns or threats in the underlying data. You can augment this with your own alert rules (or those available in the Sentinel GitHub repository), and will be able to automate response actions within the alert definitions - triggering playbooks based on Logic Apps that can notify, or remediate threats based on predefined flows of actions.
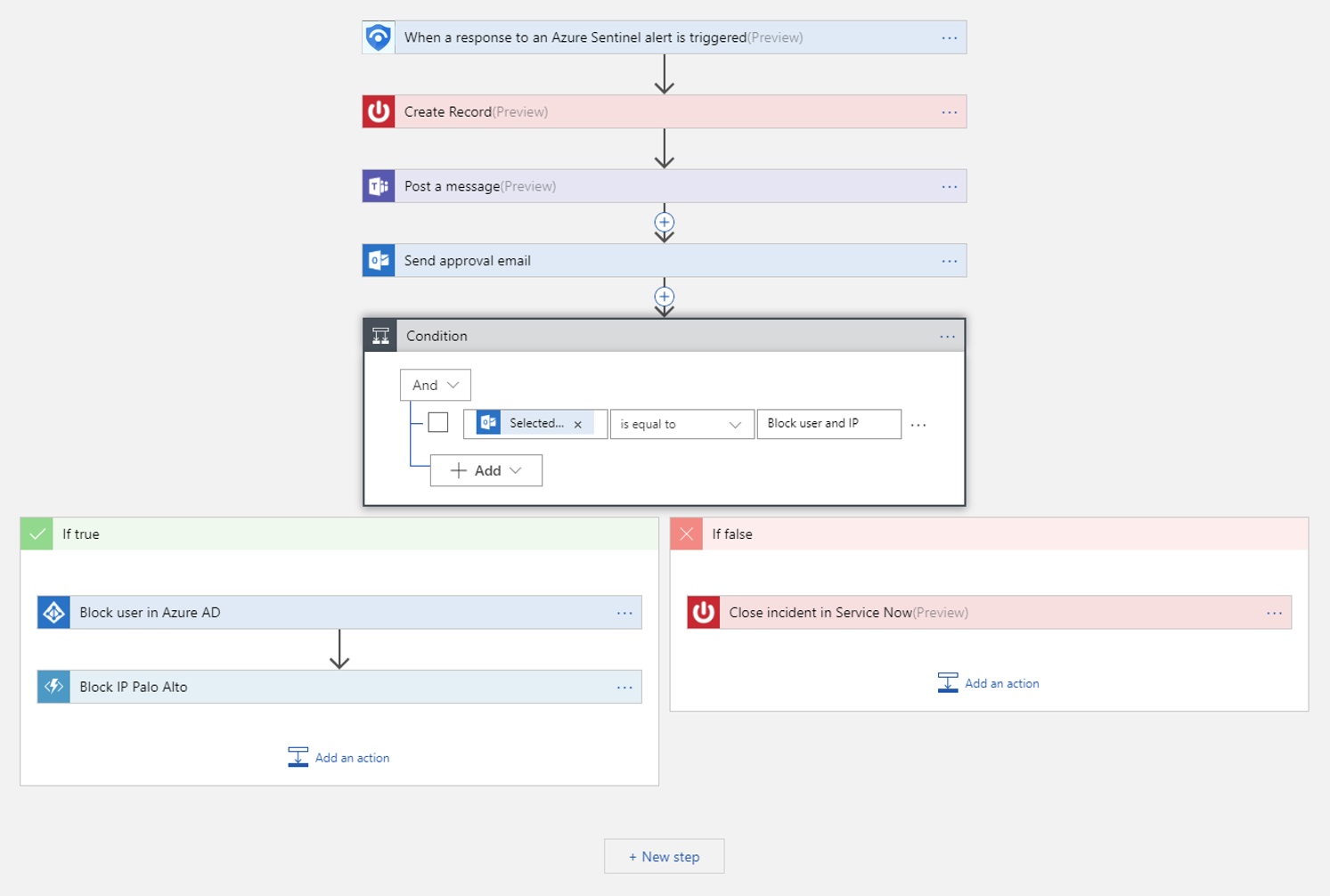
I’ve been playing with Azure Sentinel for the last 3 weeks or so, getting to grips with its capabilities and it’s limitations. Is it perfect? No. In part this is down to limitations associated with the preview (some of the headline functionality such as automated playbook execution, and visual context maps aren’t yet enabled). Is it good enough to rock the boats of some of the more established vendors though? Absolutely. What’s exciting for me is the potential for (all) organisations to be able to benefit from some of the insights that have only been available to the select few. This is about “proper” security for the masses - a very real step forward that demonstrates the power that the Cloud can bring to organisations of all shapes and sizes.
In Summary
There’s a whole lot more I could cover… not least some more technical content showing the configuration and administration experience associated with Sentinel. I intend to cover both in the coming weeks, but needless to say, if you haven’t taken a look at Sentinel just yet you really should. I’m certainly excited to share more on it with you in future posts!