8 minutes
5 Things You Should Be Doing With Azure AD

I have a lot of meetings where identity (the Azure AD variety…! :)) is a central theme. These usually start out as broader conversations on Office 365 or Cloud Security in general, but more and more frequently Azure AD is front and centre. Increasingly it’s the only topic of conversation from beginning to end…
Why? There are a host of technically exciting features - some have a basic understanding of what those are and simply want to know more. More often than not though, there are those lightbulb moments during conversation where the significance and value that Azure AD can bring becomes apparent.
So, where do you start with Azure AD? Why should you be looking at it as more than just the “authentication back end” to Office 365? I thought I’d take a moment to highlight a handful of the things I think are key to it’s success right now and which are worthy of consideration for those who want to understand how it can be used more extensively today (note: some of these features assume Azure AD Premium licensing)…
1. Authenticating Users in the Cloud
This is a key factor in the ability to drive maximum value from all that Azure AD can offer, and represents a significant shift in thinking when compared to best practices of just a few years ago. Many IT Professionals assume (with good justification in a lot of cases) that Active Directory should be king in its role as “gatekeeper” of corporate resources - even those homed in the Cloud. This has driven the design of hybrid identity solutions that incorporate technologies like ADFS or Pass-Through Authentication (PTA) in tandem with Azure AD Connect. Recent improvements to the capabilities of Azure AD, the significant security benefits that come from authenticating directly in the Cloud, and the increased desire to reduce the dependency on on-premises infrastructure have all played a part in changing this view in the last year or so though - to the extent where you can be hard pushed to justify any solution now that delegates authentication (and as a result a dependency) to the local AD.
Microsoft have published some excellent guidance on how to choose the correct authentication model for your organisation, together with some of the rationale behind the change in guidance and best practices. This can be found at aka.ms/auth-options, and includes the decision tree below which covers the available options for handling authentication:
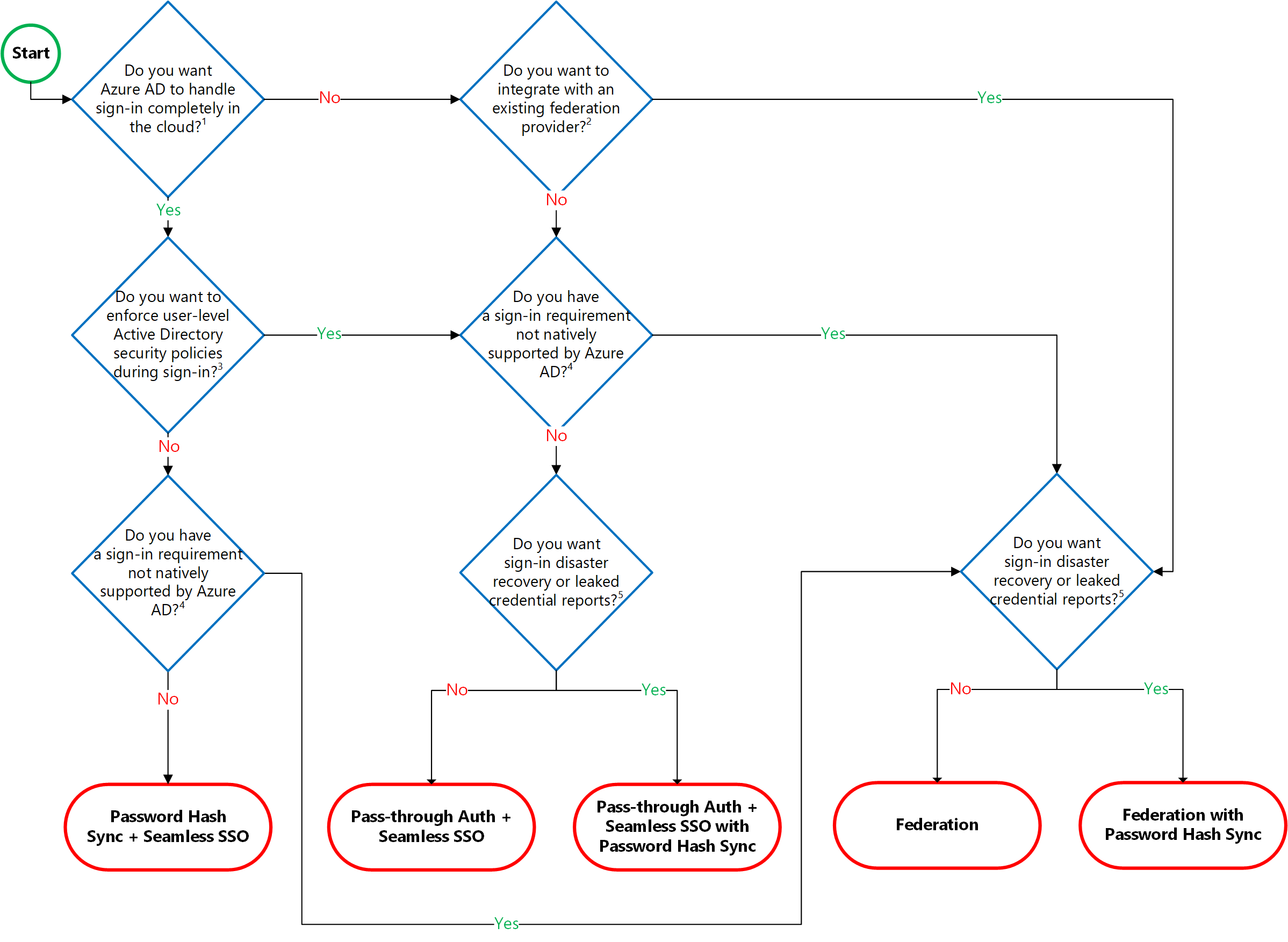
Without wanting to spoil the surprise (and in case it isn’t already evident!), there are very few standard scenarios where it doesn’t make sense to do away with ADFS / PTA in favour of Password Hash Synchronisation (PHS) and Seamless Single Sign-On (SSSO). This enables the adoption of a whole range of advanced security tools and controls; Identity Protection, native Conditional Access, the ability to take advantage of the significant Threat Intelligence Microsoft has access to through it’s processing of millions of authentication transactions each day etc… It also reduces your risk profile - removing any dependency on your on-premises Active Directory for authentication altogether. Win win 🙂
2. Integrating Applications
Azure AD has been assumed by some as being “AD in the Cloud for Office 365”. Whilst there are a host of things wrong with that statement, the sentiment also does a huge disservice to the ability of Azure AD to become the primary authentication provider for your organisation; covering a huge array of applications ranging from third-party Software as a Service applications like SAP and Salesforce, to published (on-premises) line of business applications and other Microsoft Cloud services.
The real advantage of embracing Azure AD in this way is the ability to centralise authentication - aiding the administrative overhead of dealing with starters, leavers, and general access management - and also to further secure SaaS (and other) applications through some of the advanced security controls I mentioned above, such as Conditional Access. All of this happens in a way which is friendly to the user - centralising the applications available to them using the “My Apps” portal, and taking advantage of Single Sign-On capabilities built into Azure AD to minimise the need to authenticate against each individual application.
From a governance perspective, integrating applications with Azure AD provides much needed visibility and control over third party services that may be in use - reducing the likelihood and impact of “shadow IT”, whilst simplifying the user experience where services are fully integrated through automatic user provisioning and SSO.
3. Using Privileged Identity Management (PIM)
Privileged Identity Management (PIM) is one of the hidden gems within Azure AD - arguably “hidden” due to its inclusion in only the P2 version of Azure AD Premium, but a fantastic security addition to any organisation serious about adopting the principle of least-privilege.
The premise of PIM is that access to (and exposure of) high privilege accounts should be minimised wherever possible. In practice many organisations aim to do this by leveraging dedicated administration accounts with high levels of associated security, but the fact remains that these accounts are viable targets for as long as they hold administrative rights, and also introduce internal risk through misuse (deliberate or accidental).
PIM mitigates these risks by changing the model of applying administrative permissions from one of assignment, to eligibility. In place of high numbers of permanent administrators, users can be made eligible for administrative roles - requesting and receiving access on a “just in time” basis as is needed, and subject to automatic revocation after a defined period of time.
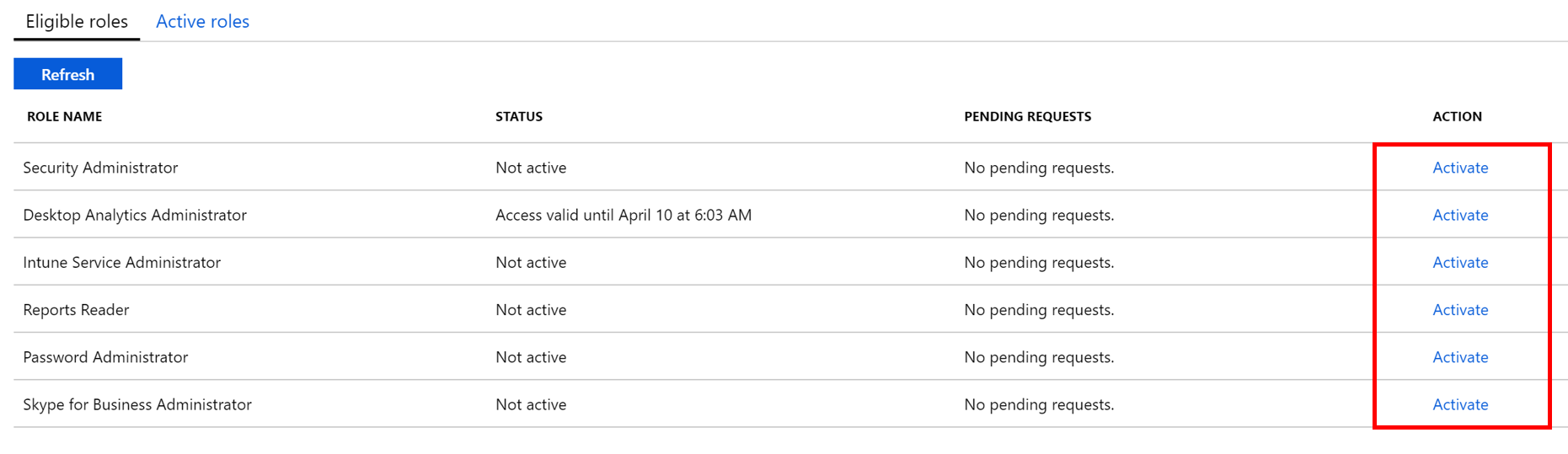
The elevation process is user initiated from the Azure portal and can be subject to administrator approval - ensuring that rights are assigned only when needed, with justification, and only for as long as is needed. Activities are recorded and can be reviewed using the Audit History view at any time. PIM is a hugely powerful capability and justifies the cost of P2 licensing in its own right (in my opinion 🙂)
4. Configuring Azure Password Protection
I dedicated a previous entry to an overview of the Azure Password Protection (APP) feature of Azure AD. You can read about it in some detail in that post if you wish, but for the uninitiated APP extends traditional password complexity requirements (in both Azure AD and Hybrid scenarios) by allowing you to determine specific words or phrases that should be banned from use in user passwords. This customised list is supplemented with the “global banned password list” - a managed database of frequently used and compromised passwords based on behaviour and attack detections across the Microsoft Cloud.
APP requires Azure AD P1 or P2 licensing in order that you can benefit fully from its capabilities, but is a fantastic way of improving the security baseline of your organisation through policing of one of the few things you can’t easily “control” as administrators. I’d always advocate the use of other controls in the authentication process to bolster security - MFA, Conditional Access etc. - but the fact remains that right now passwords are an intrinsic part of the user experience and will be for at least the short-medium term future.
5. Using Azure AD B2B Collaboration
Azure AD B2B (business-to-business) is another one of those golden, somewhat hidden (or at least not widely talked about) collaboration features, allowing you to share applications bound to your own Azure AD - such as those referred to in the “Integrating Applications” section above - with users homed in other organisations.
We’ve gotten used - over the years - to assuming that in order to provide access to resources in environments we manage, we need to create and manage local identities for those guest users. This is problematic on a couple of fronts . For one, managing users external to the organisation is fraught with challenges around licensing, security, governance, and compliance. It also leads to a poor user experience for those assigned access; one service = one credential, another service = another credential… far from elegant. Imagine a world where your one corporate identity (ideally your Azure AD account) was your token into every corporate application you needed to do your job or access the data you need. This is essentially what B2B enables, albeit there’s flexibility that doesn’t mandate the invited account to be Azure AD aligned.
Is it perfect? No. The process associated with onboarding and managing guest accounts at scale (as is sometimes needed) is clunky, but it is a significant step forward from the days of creating remote user accounts in your own domain. This limitation in particular is due an overhaul at some point this year (hopefully!) through the introduction of “Tenant Friending” - something I’ll post more about when details allow.
So there you have it… 5 quick(ish!) things you can consider using today to dramatically enhance the service you provide to end users, improve your security, and get you well on the way to adopting Azure AD in a way which you possibly didn’t imagine you could (or would). The future is bright when it comes to Azure AD with significant investment being poured into the platform and new - quite amazing - features being introduced month on month. Getting under the bonnet of what’s possible when it comes to Cloud Identity is worthwhile investment - I have absolutely no doubt there will be more and more emphasis placed on Azure AD as we step through 2019 and beyond.
Azure AD B2B Identity Microsoft Passwords PIM Security
Azure AD Identity Microsoft Security
1571 Words
18-04-2019 20:17