2 minutes
My Sign-Ins goes GA
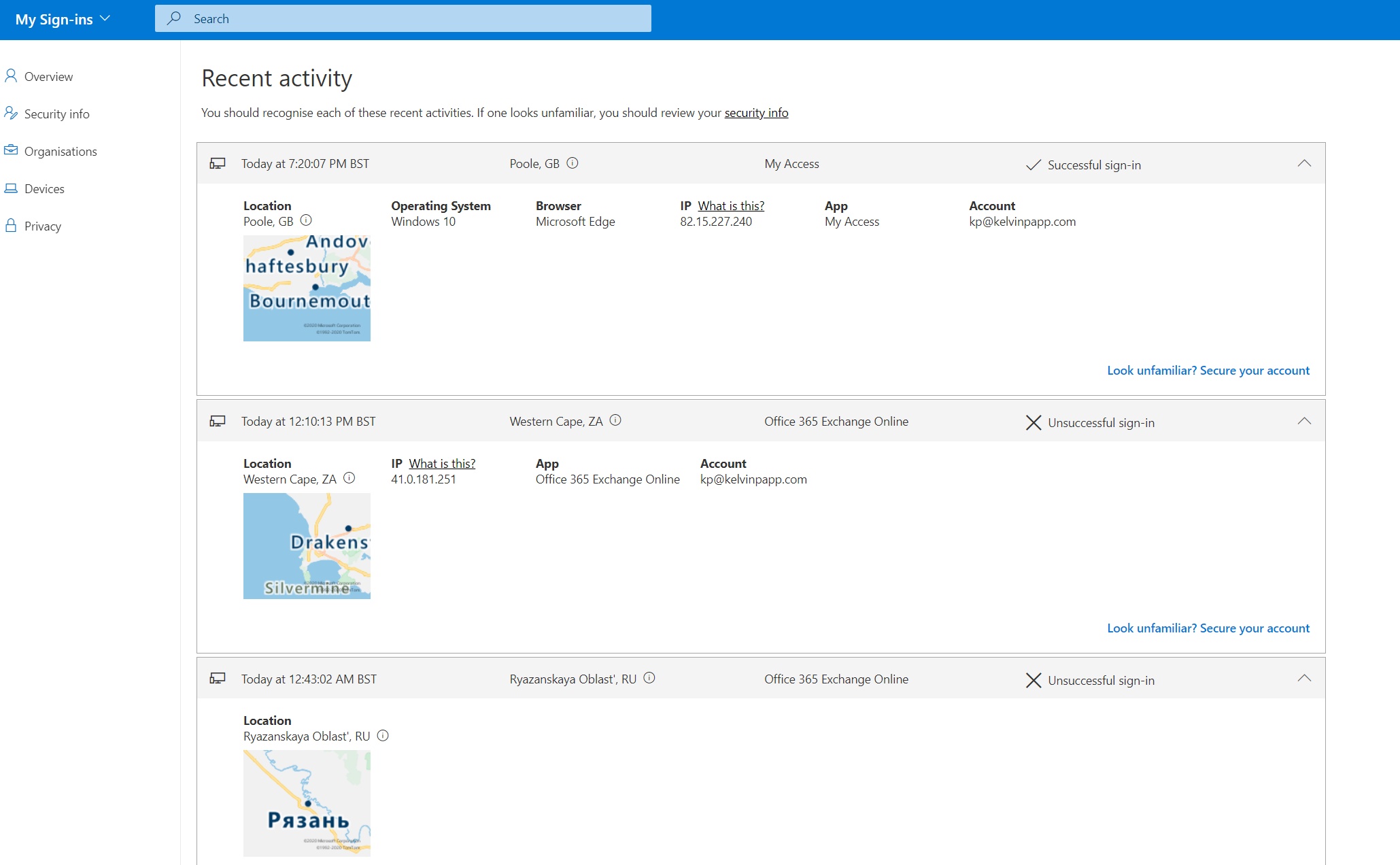
A brief, but long overdue post to reference a long awaited - but now here - feature in Azure AD! The My Sign-Ins made a Preview appearance some time ago now. Relatively feature-rich from the off, it does what it says on the tin… aggregates and shows all sign-ins for the logged in user in a clear, simple to understand dashboard. As of a few days ago, it’s (finally!) entered the world of General Availability.
What is “My Sign-Ins”?
There are a host of ways to monitor Sign-In activity from an administrative perspective - Azure AD, MCAS, and Sentinel to name a few. Until now though there’s not been an easy way for end users to review their sign-in activity. More to the point, there’s not been a way for users to easily identify and report suspicious sign-in attempts. “Is that important?” I hear you cry… well yes! Who understands their activity better, and who can take proactive action more effectively than the end user?
By reviewing sign-in history users can quickly identify attempts to exploit their account. Take the below attempts to access my account today as an example:
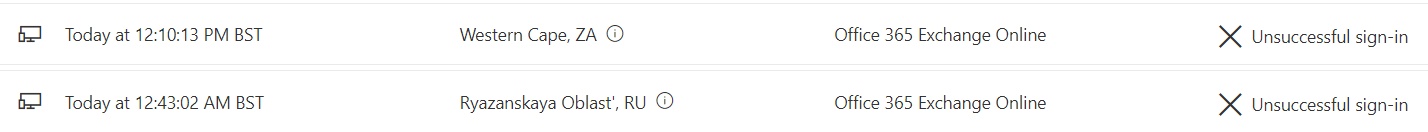
My Sign-Ins will show successful authentications which the user might interpret as suspicious. This includes the location, service, and source IP. Obviously this would never happen because you all employ Zero Trust, use MFA, and your users would deny the random sign-in request. It’s useful none the less though 😉 Should such a situation occur, users can take action directly from the My Sign-Ins portal to secure their account.
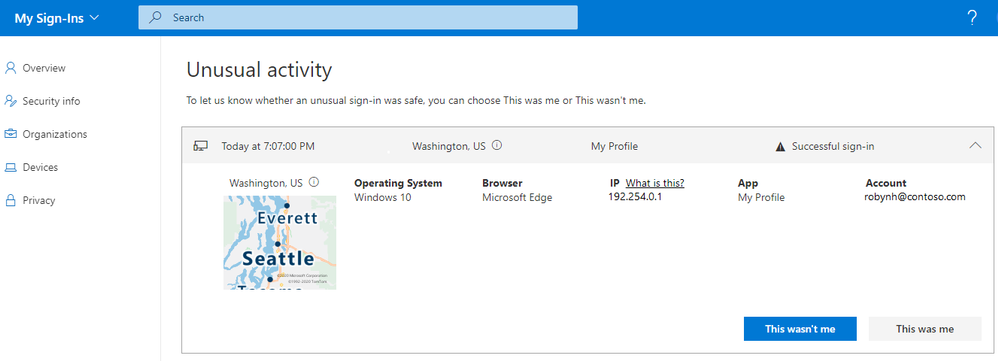
New at the point of GA is the decision to present suspicious sign-in attempts detected by Identity Protection at the top of the list. Users can specify whether the attempts were, or weren’t them. This refines the behaviour of the Identity Protection service in the case of a legitimate sign-in, and triggers account protection measures if not.
Summary
Publicising the ability for users to monitor, validate, and search their Azure AD authentications might not be top of your list, but it does add huge value in empowering users to take responsibility for the use of their accounts. Go give it a whirl!
You can read more about the announcement here in the blog post from Alex Simons.