6 minutes
Principles of Zero Trust

I’ve been meaning to write something along these lines for some time now. The concept of the changing IT perimeter is something that’s front and centre for many organisations as we approach the end of 2019. For most it’s no longer the case that data, applications, and users are secured at the network perimeter. We talk less about keeping the bad guys out, and more on the application of security at the data and identity level. This is a world away from security of old. It also requires a shift in mindset for those tasked with implementing security. For these reasons and many more we’ve seen the birth of Zero Trust as a concept. What does this actually mean though, and what are the principles associated with its implementation?
A conversation with a customer this week focussed my attention and prompted me to write down my own thoughts on it. Some argue that Zero Trust is another one of those buzz-phrases - something that will diminish as time goes by. I tend to disagree. Is it a buzz-phrase? Perhaps. Irrespective though, the principles that underpin it are significant. It’s also an essential component in the era of cloud.
Why Zero Trust?
I discussed some of the drivers for modern management in a recent presentation I delivered. Many of these principles feed into the need for a different approach towards security too, specifically:
- Mobility. Users increasingly have an expectation of working remotely, and at different times of the day and night.
- Modern Devices. In the same vein, users now expect to be able to access and work on corporate content across an increasingly wide array of mobile, laptop, and desktop devices.
- Expectations. Corporate IT shouldn’t be a step behind. Newer ways of working, the ability to share and collaborate on data, and the availability of services from anywhere / at any time are available at home. Users expect this in the workplace too.
Accommodating these new approaches to working requires a different approach to security. One which does away with the assumption that we consume IT in a way which is secure by default. Devices, applications, and data which sit outside of the traditional perimeter are the new norm. This is where Zero Trust comes in to play.
So what is Zero Trust?
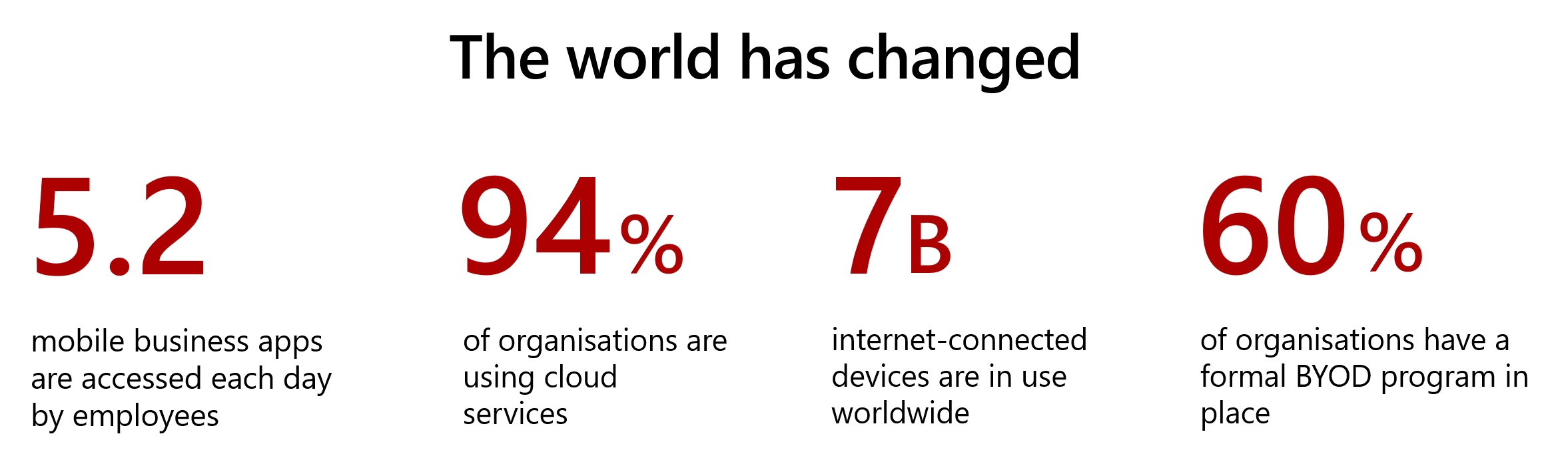
The statistics above were displayed at a session I attended at Microsoft Ignite: Zero Hype – Taking practical steps towards Zero Trust. They do a great job of further framing some of the comments I make above. The session went on to discuss Zero Trust in more detail. There was a specific focus on dispelling some of the myths and FUD associated with Zero Trust across our industry; this is a big issue in my opinion. I’d really encourage you to watch the session if you get the chance.
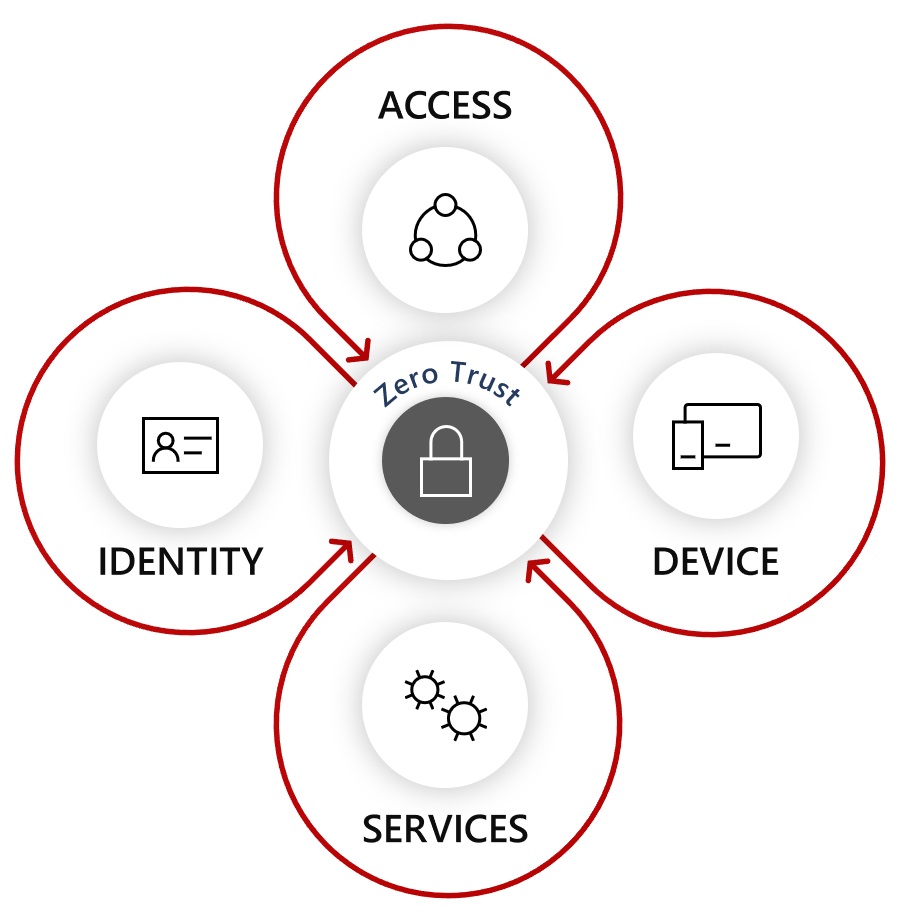
At it’s core, Zero Trust is an approach that encourages verification at as many layers as possible when accessing resources. It promotes strong identity, device health attestation, and the principle of least privilege. It also encourages consideration of the assumption that every access attempt is a potential risk. This approach challenges traditional approaches to identity and security. It also brings these approaches up to date with modern ways of delivering data and applications to users - notably those that are cloud based. Ultimately the concept of Zero Trust promotes a good security posture by taking an “assume the worst” stance.
What Zero Trust is not is something you will ever “be”, or something you can pay a vendor to provide for you. It’s not a literal thing, or something you can achieve overnight. By taking into account basic ZT principles though, you can dramatically reduce your chance of being caught out by the changing behaviours of the modern workforce. Those in heavily governed sectors are likely to find that embracing a Zero Trust mentality will aid the adoption of cloud. From my personal experience, it will certainly appease some of the Security team 🙂
Your Journey
So how do you get there? What, at a practical level, can you do to kick off your Zero Trust strategy? There are some key areas to target, the first of which is that mindset change I mentioned above… Change your way of thinking when it comes to security to one that assumes everything is a risk. Think of everything as a cloud service, and aim to implement the practices you might be already be associating with select applications, across the board.
I made reference to a bunch of things you should be doing with Azure AD in a previous post. Start with these and strengthen your approach to identity. Integrate applications so you you can secure them consistently, and implement PIM to ensure least privilege. Identity is a great place to start, and a fundamental when it comes to secure cloud adoption.
Focus also on device attestation and compliance. Use solutions like Microsoft Endpoint Manager (Intune) to manage devices, and impose compliance baselines. Feed these back into your identity platform to make informed decisions around when, and to what level you allow access to your resources.
Understand your applications. Invest in a CASB solution like Microsoft Cloud App Security (MCAS) so you can identify, and manage the services your end users elect to use. Again, integrate these with your identity and device management solutions so you can invoke real-time controls based on user behaviour and activities.
Assume that your data will end up outside of your perimeter. Take advantage of data classification solutions like Microsoft Information Protection to enable document level encryption and controls that extend your control beyond the traditional edge.
In Conclusion
These are just a handful of the things that you can do to get started on your Zero Trust journey. The key message from my perspective is that it’s exactly that - a journey. There’s no hard and fast rule-book. There’s no one solution you can go out there and buy which will help you to “be” Zero Trust. There are however, a number of really simple to deploy features that many organisations will have access to already. Layer these together, have the right mentality, and the end result is that Zero Trust - buzzword or not - is something that will greatly aid your overall security posture.
I hope this post has been useful at dispelling some myths around Zero Trust. What it is, what it’s not, and crucially how you can begin to embrace it yourselves. By way of additional reading I’d urge you to take a look at the following other resources:
- This session from Microsoft Ignite: Zero Hype – Taking practical steps towards Zero Trust. The source of a couple of the graphics in this post, and delivered by the excellent Alex Weinert.
- This additional Ignite session: Implementing a zero trust security model at Microsoft which discusses the transition Microsoft have made towards Zero Trust within their organisation.
- Microsoft’s Zero Trust Portal: aka.ms/Zero-Trust
As always, comments and feedback welcome!
Azure AD Cloud App Security Identity Intune Microsoft Security Zero Trust
Azure AD Identity Microsoft Security
1165 Words
23-11-2019 19:07