5 minutes
Securing Twitter with Microsoft Authenticator

A fairly topical post today in response to yesterday’s news that Twitter CEO Jack Dorsey’s account was “hacked”. I use that term loosely as it’s since transpired the method used was actually the SIM swap scam (explained further below). None the less, it serves to highlight the importance of account security and should be a reminder to us all of the lengths that “hackers” will go to. Particularly for those in the public eye. I thought I’d take a moment to run through some simple steps you can take to enable the Microsoft Authenticator app to be used for securing Twitter.
A caveat…
It’s important to note that in this example the “weakness” exploited was the text update system Twitter uses, not the account. Whilst most of us are used to app / web based consumption of Twitter, the text system is still widely used in developing countries. Using this method you can tweet by sending an SMS from your registered mobile number - no sign in required. Here Jack’s number was ported to a new SIM and intercepted, allowing the perpetrators to circumvent traditional security measures. Crude, but actually quite simple - and clearly effective 🙂 Whilst the steps outlined in this post don’t prevent this form of exploit, they’re every bit as important. They’re also simple, and dramatically reduce your likelihood of becoming a victim.
What can you do?
As you’ll have noted by now, a recurring theme of this blog is security. I’ve talked in various posts about features in Azure AD like Conditional Access to enforce multi-factor authentication (MFA) on sign-ins to Azure AD. This is all well and good for business applications, but what about personal accounts or services? We increasingly see MFA recommended everywhere. Email accounts, banking, social media applications, websites. What few realise though, is that it’s possible to condense the number of methods used.
Do you really need 5+ mobile apps to prove who you say you are? I did, not too long ago. I now have 2… (and only then because HMRC insist on using their own application 😬).
In this post I want to focus on securing Twitter using the Microsoft Authenticator - for two reasons:
- Lots of people are vulnerable to account compromise due to not having MFA enabled for Twitter
- Where MFA is turned on it defaults to SMS validation… which just feels a bit 00s 😉
Configuring Twitter MFA to use Microsoft Authenticator
Configuring Twitter to use MFA via the Microsoft Authenticator is really simple. As a pre-requisite you need to have verified your mobile number and email address. I’m also going to assume that you have the Authenticator app installed on your mobile. Screenshots below are taken from an iOS device, but will look similar on Android for those of you on the dark side 🙂
In the Twitter app, navigate to Settings and Privacy > Account. Assuming you’ve verified your Phone / Email details both will be populated. Select “Security”, and then “Login Verification”. Your app will most likely look like this:
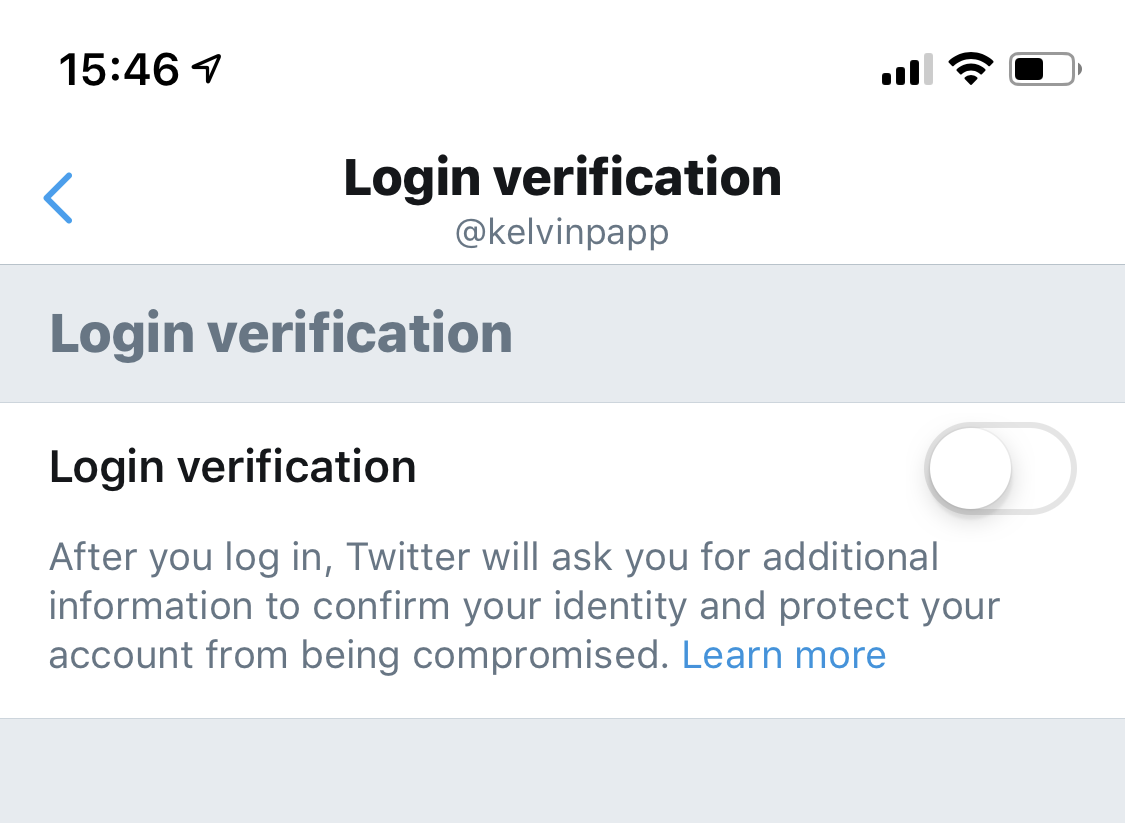
Toggle “Login Verification” to on and you’ll be asked to confirm acceptance that you’ll need your phone to sign in to Twitter. You’ll then be walked through a short wizard to enable SMS codes (initially) during which you’ll need to verify your current Twitter password and mobile (via SMS). On completion I strongly suggest you generate a Backup Code when prompted. This will be your only route in should you lose your phone, or access to your Authenticator app… you have been warned!
Once finished, Login Verification should look as follows:
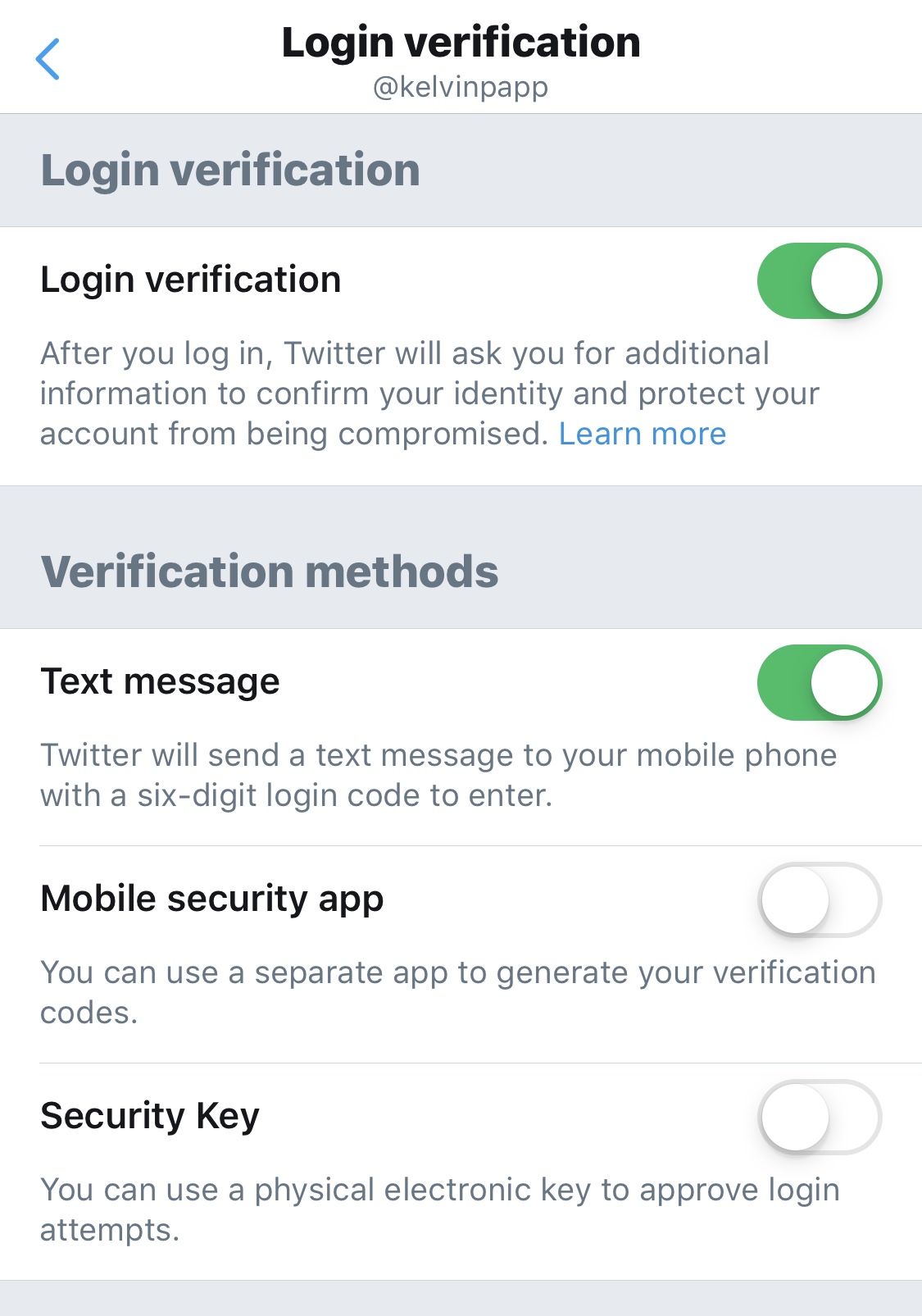
Here’s where we’re going to integrate Microsoft Authenticator, and optionally disable SMS. Toggle “Mobile Security App” to on. Another wizard will launch to walk you through activating your Authenticator app for Twitter. After clicking “Set up Now” you’ll be redirected into Microsoft Authenticator. You should now see a Twitter entry and corresponding code:
To complete setup, verify that the code functions by entering the current digits back into the setup wizard. On redirection back into the Twitter app you should see that “Mobile Security App” is enabled. You can choose to disable SMS notifications if you wish, at this point:
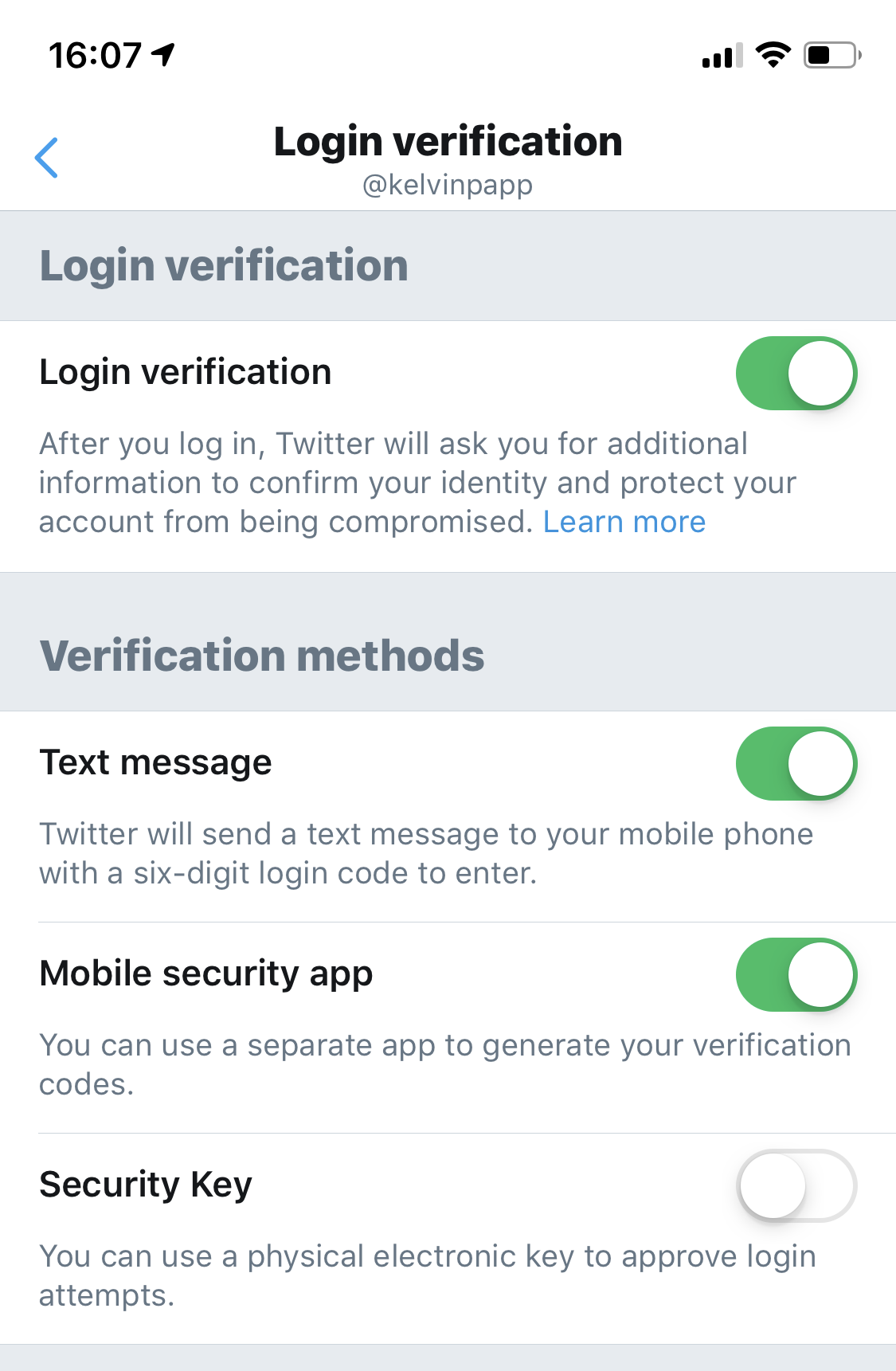
From this point onwards, whenever you login to Twitter you’ll be asked to verify your identity using the code from your Authenticator app. Sadly this doesn’t extend to push notifications (at this point in time).
Summary
Obviously securing Twitter is one example of many. There are multiple services that let you use your own authenticator app(s) in place of SMS or default code generators. For me, securing as many of my online services as possible via MFA is a no-brainer. If I can then consolidate them into a single (or a handful) of apps in lieu of text messages / phone calls / proprietary applications, then so much the better ?
The bottom line is simple. Whilst the majority of us aren’t targets in the way that individuals like Jack Dorsey are, we bear our own responsibility for securing our online identities. In most cases this can be done simply, and using tools / devices that are already at your disposal.
Don’t become a victim!
Authentication Authenticator Identity MFA Microsoft Passwords Security SMS Twitter
863 Words
31-08-2019 15:35