4 minutes
Shared YouTube with Azure AD
A slightly random entry today, triggered largely by a post on the Microsoft Tech Community forums this week. The post in question was asking whether it was possible to authenticate to YouTube with Azure AD - specifically, whether it was possible to securely access a shared account without divulging credentials. For many organisations shared accounts are a necessity, particularly with reference to platforms like Twitter and YouTube. Teams of people often contribute content to these sites, with credentials routinely shared. This is problematic when it comes to leavers - triggering a need for passwords to be reset which then need to be memorised all over again. Azure AD provides a neat way around this which we’ll discuss below.
I’ve written in the past about the advantages associated with integrating SaaS applications with Azure AD. The solution here is an extension of that principle. I expected to be able to quickly track down a guide on how to implement this for the poster, but struggled to do so. I jotted down a quick response and decided I’d pop my own guide together instead. A couple of days later, here we are…
The specific feature I want to cover is the ability for credentials to be bound to a user for an application in Azure AD. The application portal is one of Azure AD’s most useful features (in my opinion). It provides a single point of access to all corporate applications - Microsoft or otherwise. In this case we can create a link to YouTube that’s published to users. When clicked the user will automatically be signed in. Unlike a “true” SSO app, this won’t authenticate using the users Azure AD credentials. Instead, we’ll allocate the username and password which will be populated automatically when the link is clicked. We’ll also benefit from additional audit tools - with the ability to track usage through app sign-in logs.
Integrating YouTube with Azure AD
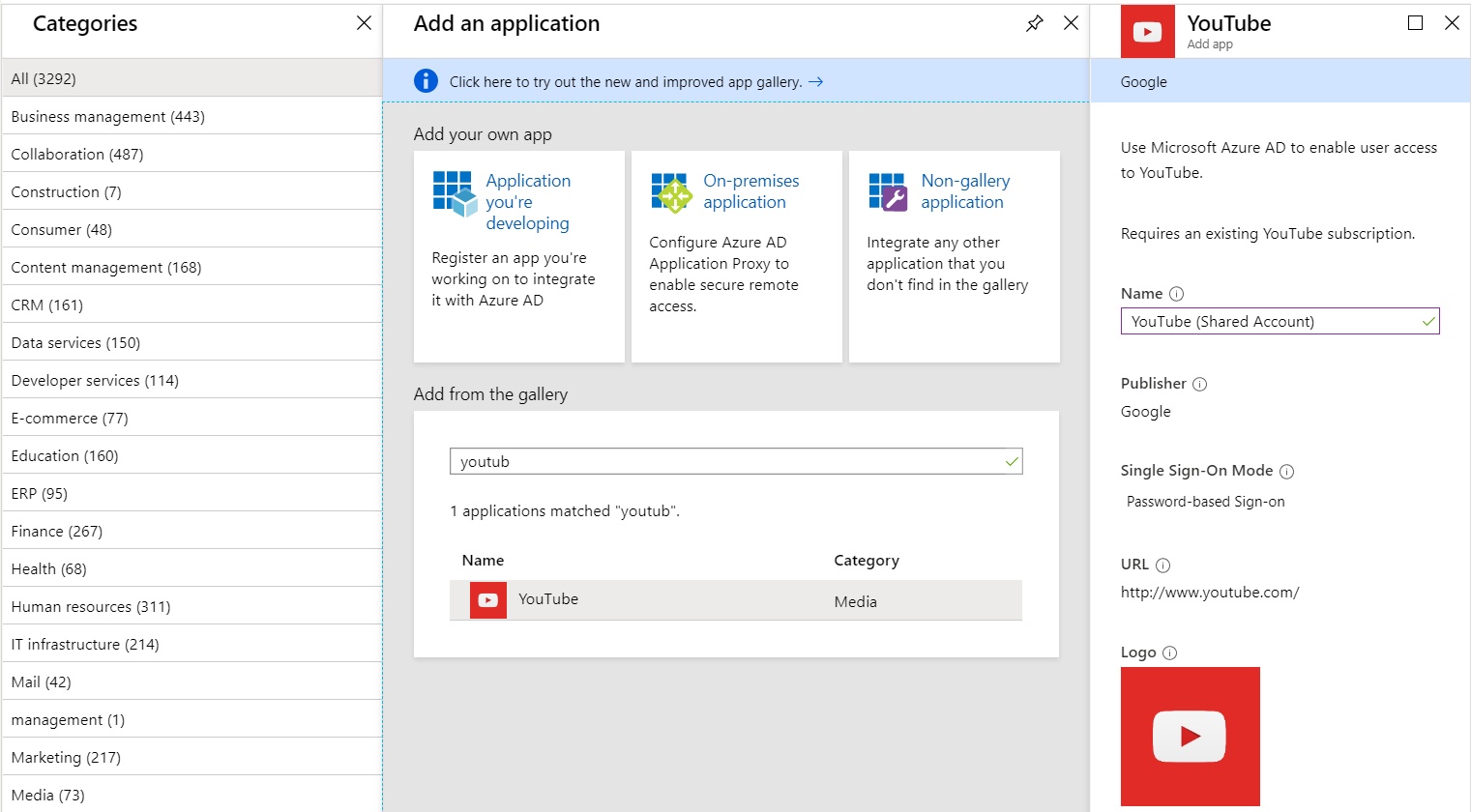
The first step is to navigate to our Azure AD portal and select the Enterprise Applications section. We are going to add a new application for YouTube by selecting “New Application” and searching for YouTube in the gallery:

After clicking “add”, the YouTube app will be registered with Azure AD, after which we can modify several properties to make it available. Select YouTube from the list of Enterprise applications and you should be presented with the overview page:
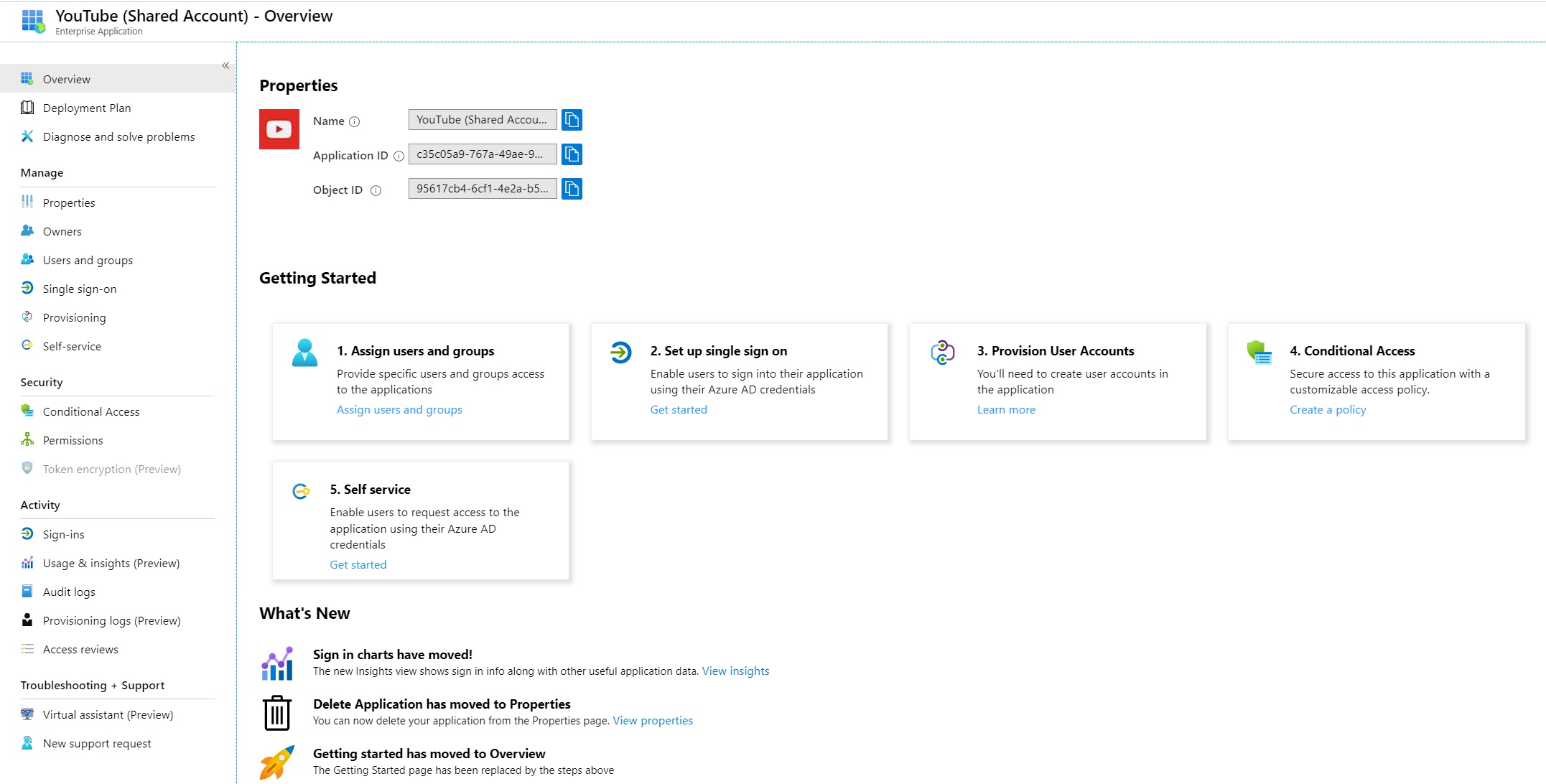
There are a couple of changes to the default configuration. We need to make it accessible to users, and we need to provide our shared account credentials. First of all we’re going to configure the application so it will present credentials when clicked. By default, think of the app as a dumb link - it will direct users to YouTube, but they will need to manually login. As mentioned earlier we don’t want to authenticate using Azure AD. Instead, we want to select “Password-based” sign-in from the Single sign-on section of the app:
This sets the URL the application will call when clicked by the user - directing us to the Google sign-in page:
We then need to assign our users (or groups) to the app. Navigate to “Users and groups” within the application properties and add the relevant users:
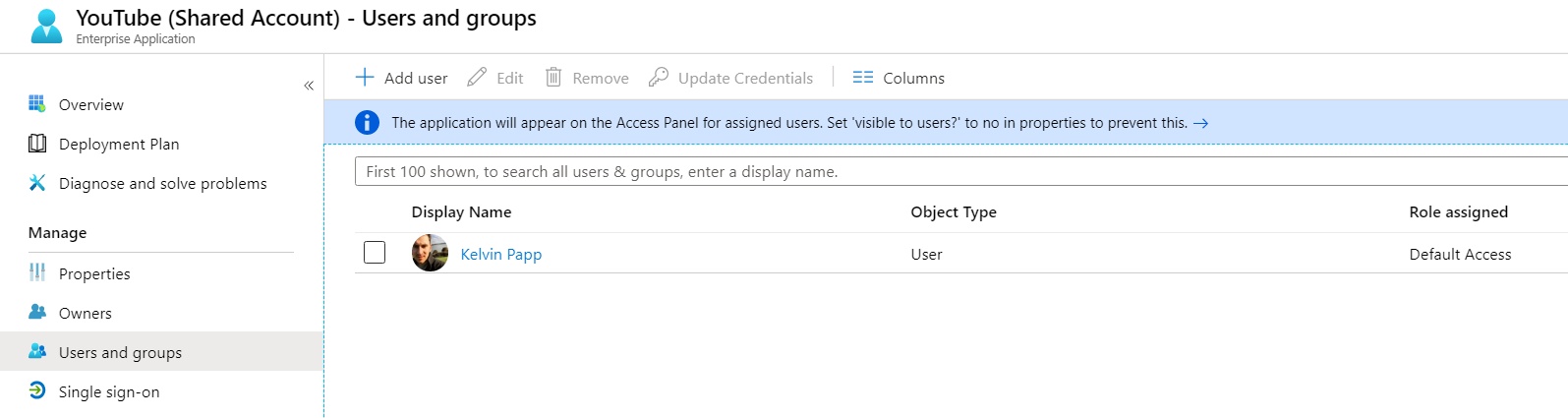
The next step is the key one. We need to assign our shared account username and password to the user or group. We do this by selecting the user (or group) and clicking “Update Credentials”. In the dialogue that appears we can insert the username and password for our YouTube account:
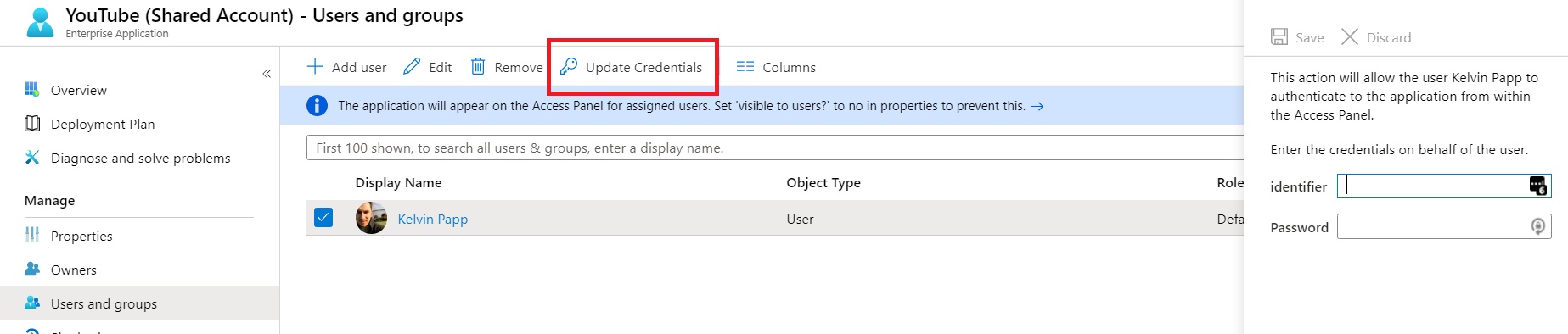
Click save, and we’re ready to test…
Testing the Azure AD Application
Sign in to the Microsoft MyApps portal myapps.microsoft.com with a user account assigned to the application. You should see the new YouTube application listed amongst your assigned applications:

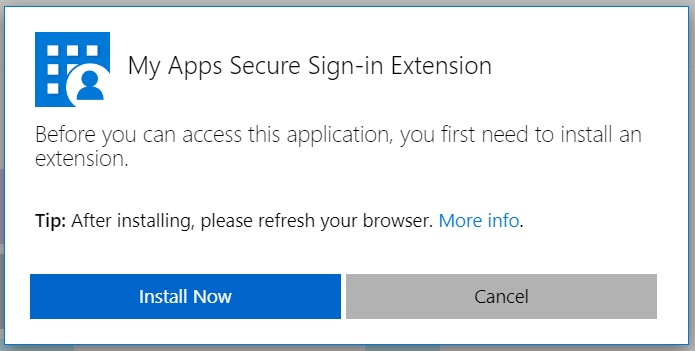
If you don’t already have it installed, you will need to install the MyApps Secure Sign-In Extension. Your browser will prompt you if this is the case:
Once installed, and after a brief pause when you select your Azure AD application, you should be directed to the Google sign-in page for YouTube. The credentials bound to the user in the previous “update credentials” step will be replayed automatically, and you will be signed in with your shared account.
Summary
This is a really neat use of Azure AD to both simplify and better secure access to shared YouTube accounts for organisations. The same logic can also be applied to other web based services (e.g. Twitter). In this example the username and password combination is never made directly available to the end user. We can assign / unassign the application as necessary, and ultimately be assured that if a user leaves the organisation or no longer needs access, the underlying credentials remain secure.
I hope you’ve found this post useful, feel free to ask away in the comments if you have any follow up questions.
Authentication Azure AD Identity Microsoft Microsoft 365 Passwords
Azure AD Identity Management Microsoft
813 Words
15-12-2019 17:35