4 minutes
What is FIDO2 and why should you care?

FIDO2 is something I’ve referenced previously on here, albeit not in too much detail. Many only take a passing interest in what this standard is and its importance when it comes to popular concepts like passwordless authentication. This was confirmed to me today as I found myself browsing through the responses to a recent @SwiftOnSecurity post on Twitter:
LastPass is basically a dead product they don’t support even U2F, much less FIDO or FIDO2.
— SwiftOnSecurity (@SwiftOnSecurity) February 15, 2020
The crux of the conversation that followed was the lack of support LastPass has when it comes to supporting FIDO2 standards. Why is this important though, and why should it be a factor in how you select services (like password managers)?
For the record, I’m a longstanding (premium) user of LastPass. It’s served me well over the years and still has some neat features not available in many alternatives. That said, the lack of progress when it comes to support for passwordless / WebAuthN has been a frustration for many (myself included). Thinking and principles around authentication security have matured significantly in recent years. Multi-Factor Authentication (MFA) has become mainstream, as have friction-less sign-in solutions like Windows Hello. FIDO2 is a major contributor to this; in terms of both user experience, and security standards. As people become more aware and less accepting of “poor” progression on these fronts, the importance of adopting new standards become all the more important.
The response from LastPass has been woefully inadequate, with many informed users taking services elsewhere as a result.
So what is FIDO2?
Before we talk FIDO2, we should first cover the basics of the FIDO Alliance and it’s contribution to date. FIDO is short for “Fast Identity Online”, an industry alliance focussed on improving authentication standards. It’s ultimate objective is minimising (or removing) passwords altogether. This is made possible through the adoption of common standards across the industry.
The original FIDO standard attempted to reduce the importance of passwords through an approach built on public key cryptography. This is known as the Universal Authentication Framework (UAF). Unlike traditional authentication approaches that require the transmission of a password, the FIDO standard relies on a local action. This can be the providing of a fingerprint, entering of a PIN, inserting a security key etc. and results in access a locally held private key. This key is used to sign an authentication request, which can be decrypted by the public key available to the service.
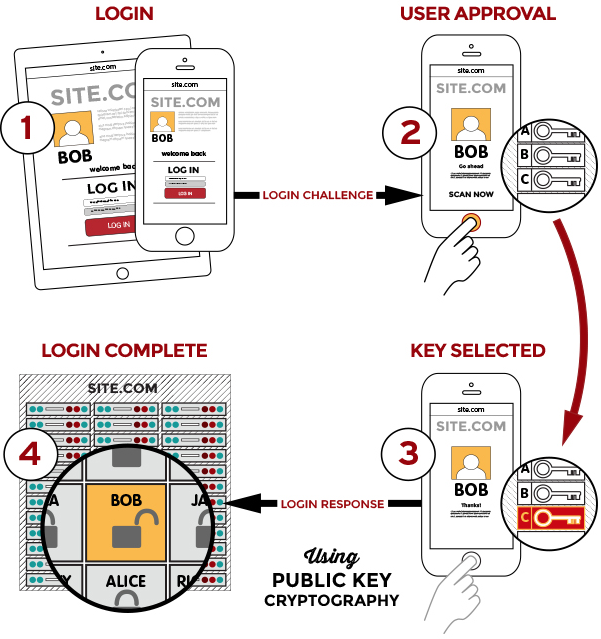
UAF has been enhanced with the Universal 2nd Factor (U2F) standard. This provides support for two-factor authentication (2FA) alongside UAF, and replaces traditional OTP solutions with USB, NFC, or Bluetooth equivalents. The net result is a streamlined experience for the end user, minimal prompts or interaction.
It’s with that background, that we can discuss FIDO2. This new(er) standard builds on FIDO 1.0. Leveraging U2F alongside a new web API called Web Authentication (WebAuthn), FIDO2 allows web applications to use public-key encryption and authenticators directly. This is integrated into browsers, allowing users to log in using biometrics, mobile apps or FIDO2 security keys. There’s no need for a username or a password… true seamless, friction-less, and passwordless authentication!
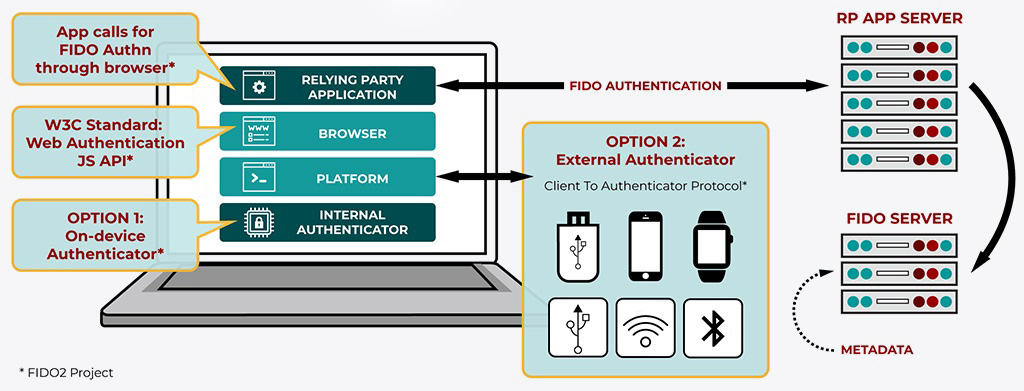
What does it mean for you?
Coming full circle, let’s apply this logic to services like LastPass. When compliant with FIDO2, no password is exchanged with the service at logon. The presence of a FIDO2 device, or access from a FIDO2 certified platform (such as a Windows Hello enabled laptop) allows access to the service. This is achieved in a manner which also satisfies MFA. In the context of a service entrusted with sensitive information this should be a given in 2020. Certainly far better than a master password that can be compromised, or a clunky integration of 2FA via an OTP code…
FIDO2 will change the way we consume and authenticate against online services. The backing of organisations like Microsoft, and integration of FIDO2 into platforms and applications means that this level of security is capable of being mainstream… if adopted by application vendors.
Translating this into a real world example, we can consider the way Microsoft have embedded FIDO2 and WebAuthn into Windows 10. As an end user I can walk up to any Azure AD joined device in my organisation and present my FIDO2 compliant YubiKey. Coupling this “something I have” with “something I know” (a PIN), I can be logged into the device without mention of a username or password. The same is true when accessing online services backed by Azure AD… Insert the key, enter the PIN and you’re in. No fuss, ultra secure.
The LastPass example may be of minor relevance to most of you reading. The principle is universal though. Open standards like FIDO2 provide the mechanism for simplicity, security, and minimise the risk of data breach. End users might not appreciate the detail, but I can guarantee you they’ll appreciate the ease. Your CISO will thank you too… 🙂