2 minutes
Security Registration & CA
A brief post from me today to highlight something I stumbled across this week. I’ve not seen any formal communication from Microsoft on this change (although I’m sure it’s lurking somewhere), but it strikes me as a key new feature many will want to enable…
The process for registering Security Information is one which should be ultra secure. Control of this information allows the account password to be reset, or MFA challenges to be accepted. In theory it is; triggered as soon as it applies and subject to continual prompts (or blocked access) until complete. In practice it’s always unnerved me that any user, anywhere in the world can gain access and (theoretical) control of an account before registration takes place. Of course we can reset fraudulent or erroneous registrations, but minimising the chance is surely better. Now you can!
Security Information Registration Update
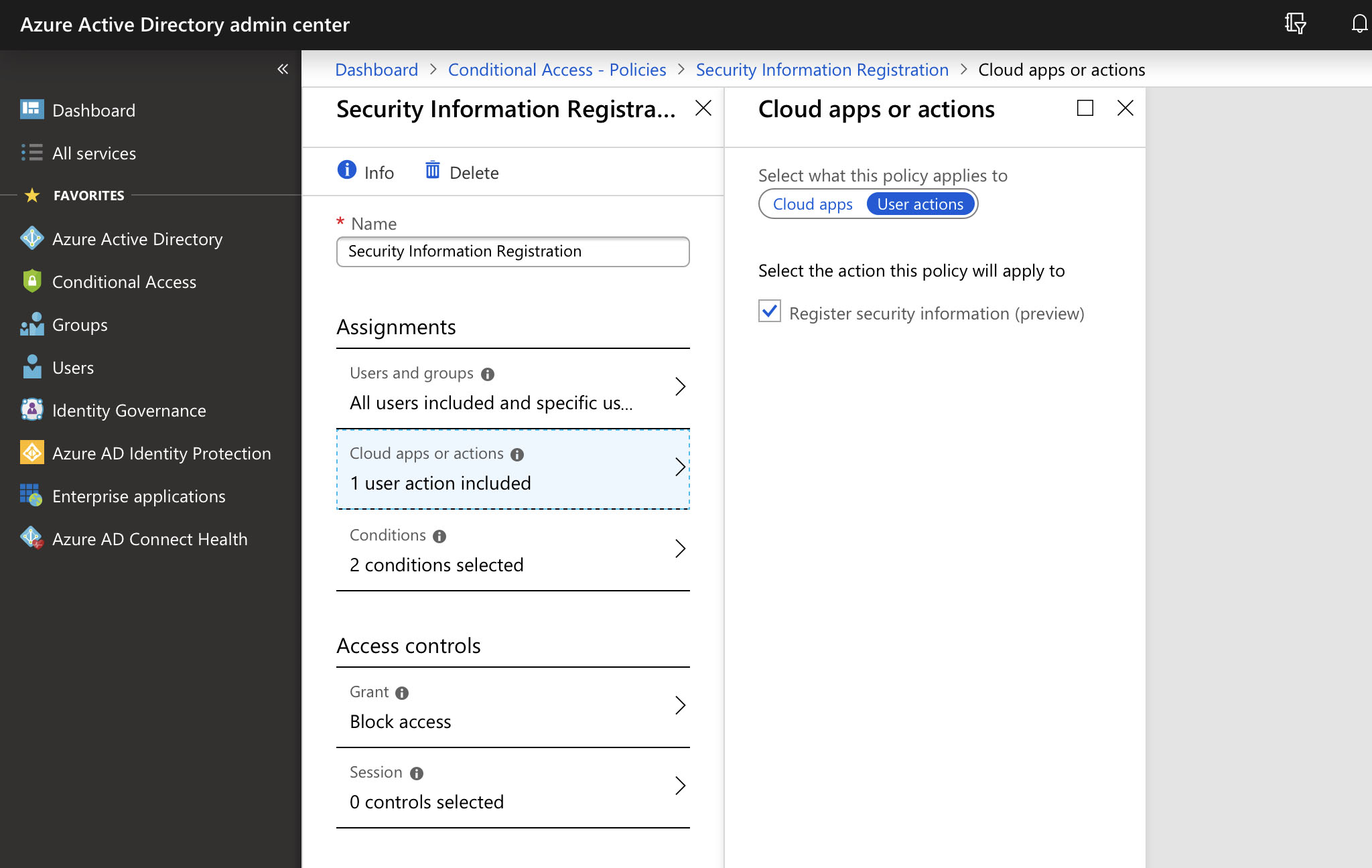
The control in question is a new setting within Azure AD Conditional Access. Under “Cloud apps or actions” we have a new “User Action” we can apply policy to: “Register security information (preview)”. Using this in tandem with conditions that specify locations or approved devices allows us to block registrations that don’t match criteria we set. For example those from users off of the corporate network, or those initiated from devices that are non-compliant.
Once enabled users who satisfy the username / password challenge but are required to enrol Security Information (or provide MFA) will receive a message. This states that whilst the sign-in was successful, the criteria for access wasn’t met ?
If you’re in a position where you can limit registration to trusted scenarios this is a great way of further securing your users. It’s not for everyone, but will accommodate a good proportion who onboard users locally. Go and have a play!
For those interested in other Azure AD recommendations, I discussed the 5 Things You Should Be Doing With Azure AD in a recent post. If I was writing it again this feature would get a mention. For those that haven’t read it already, why not spare 5 minutes to find out why I think many are missing out!
Azure AD Conditional Access Identity MFA Microsoft Security
Azure AD Identity Microsoft Security
357 Words
11-05-2019 18:18